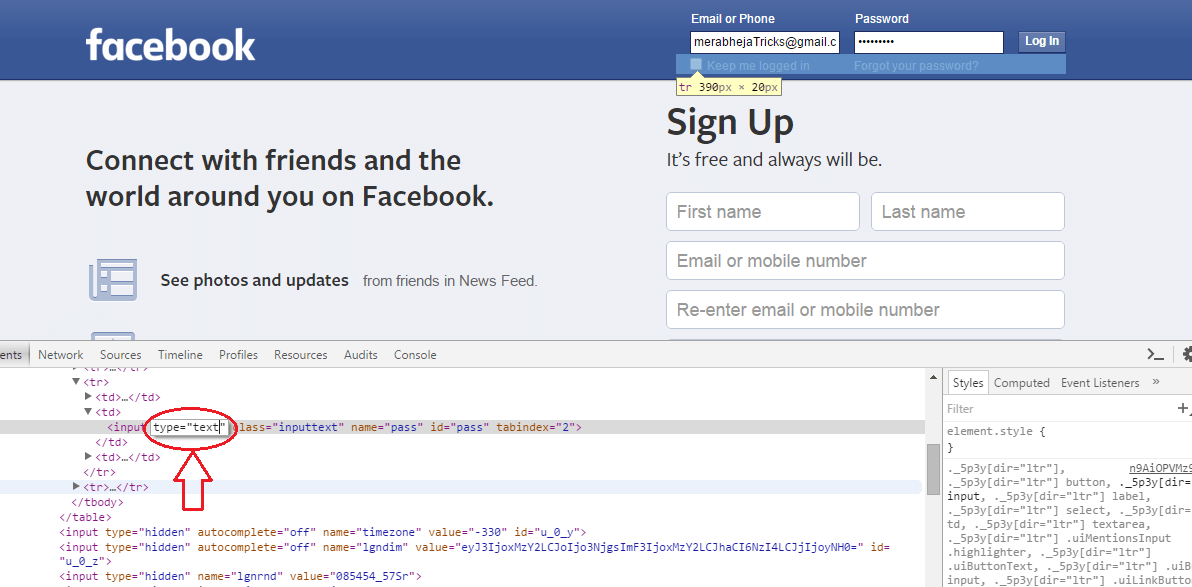
- Intext Facebook Password Page
- Intext Password Txt
- Intext Facebook Passwords
- Intext Email Password Facebook
- Intext Facebook Password App
Google Dork: filetype:sql intext:password pass passwd intext:username intext:INSERT INTO `users` VALUES Author: screetsec Description: This dork allow you to specific find file contains Username, Password, Secret Keys and allows you to search for sql configuration file. Password dictionaries. These are dictionaries that come with tools/worms/etc, designed for cracking passwords. As far as I know, I'm not breaking any licensing agreements by mirroring them with credit; if you don't want me to host one of these files, let me know and I'll remove it. Analytics cookies. We use analytics cookies to understand how you use our websites so we can make them better, e.g. They're used to gather information about the pages you visit and how many clicks you need to accomplish a task. Username=checking password=hacking username=rahulabvp90@gmail.com password=yadavrahul username=rahulabvp90@gmail.com password=yadavrahul username=shyamraj4757@yahoo.com password=27902999 username=rahul Kumar password=15081971 username=rahul Kumar password=15081971 username=rahulabvp90@gmail.com password=yadavrahul username= password= username=dmohanty90@gmail.com password=annaund1991 username. Intext-email-password-ext (1).txt - Free download as Text File (.txt), PDF File (.pdf) or read online for free.
- 2Leaked passwords
- 3Miscellaneous non-hacking dictionaries
Password dictionaries
These are dictionaries that come with tools/worms/etc, designed for cracking passwords. As far as I know, I'm not breaking any licensing agreements by mirroring them with credit; if you don't want me to host one of these files, let me know and I'll remove it.
| Name | Compressed | Uncompressed | Notes |
| John the Ripper | john.txt.bz2 (10,934 bytes) | n/a | Simple, extremely good, designed to be modified |
| Cain & Abel | cain.txt.bz2 (1,069,968 bytes) | n/a | Fairly comprehensive, not ordered |
| Conficker worm | conficker.txt.bz2 (1411 bytes) | n/a | Used by conficker worm to spread -- low quality |
| 500 worst passwords | 500-worst-passwords.txt.bz2 (1868 bytes) | n/a | |
| 370 Banned Twitter passwords | twitter-banned.txt.bz2 (1509 bytes) | n/a |
Leaked passwords
Passwords that were leaked or stolen from sites. I'm hosting them because it seems like nobody else does (hopefully it isn't because hosting them is illegal :)). Naturally, I'm not the one who stole these; I simply found them online, removed any names/email addresses/etc (I don't see any reason to supply usernames -- if you do have a good reason, email me (ron-at-skullsecurity.net) and I'll see if I have them.
The best use of these is to generate or test password lists.
Note: The dates are approximate.
| Name | Compressed | Uncompressed | Date | Notes |
| Rockyou | rockyou.txt.bz2 (60,498,886 bytes) | n/a | 2009-12 | Best list available; huge, stolen unencrypted |
| Rockyou with count | rockyou-withcount.txt.bz2 (59,500,255 bytes) | n/a | ||
| phpbb | phpbb.txt.bz2 (868,606 bytes) | n/a | 2009-01 | Ordered by commonness Cracked from md5 by Brandon Enright (97%+ coverage) |
| phpbb with count | phpbb-withcount.txt.bz2 (872,867 bytes) | n/a | ||
| phpbb with md5 | phpbb-withmd5.txt.bz2 (4,117,887 bytes) | n/a | ||
| MySpace | myspace.txt.bz2 (175,970 bytes) | n/a | 2006-10 | Captured via phishing |
| MySpace - with count | myspace-withcount.txt.bz2 (179,929 bytes) | n/a | ||
| Hotmail | hotmail.txt.bz2 (47,195 bytes) | n/a | Unknown | Isn't clearly understood how these were stolen |
| Hotmail with count | hotmail-withcount.txt.bz2 (47,975 bytes) | n/a | ||
| Faithwriters | faithwriters.txt.bz2 (39,327 bytes) | n/a | 2009-03 | Religious passwords |
| Faithwriters - with count | faithwriters-withcount.txt.bz2 (40,233 bytes) | n/a | ||
| Elitehacker | elitehacker.txt.bz2 (3,690 bytes) | n/a | 2009-07 | Part of zf05.txt |
| Elitehacker - with count | elitehacker-withcount.txt.bz2 (3,846 bytes) | n/a | ||
| Hak5 | hak5.txt.bz2 (16,490 bytes) | n/a | 2009-07 | Part of zf05.txt |
| Hak5 - with count | hak5-withcount.txt.bz2 (16,947 bytes) | n/a | ||
| Älypää | alypaa.txt.bz2 (5,178 bytes) | n/a | 2010-03 | Finnish passwords |
| alypaa - with count | alypaa-withcount.txt.bz2 (6,013 bytes) | n/a | ||
| Facebook (Pastebay) | facebook-pastebay.txt.bz2 (375 bytes) | n/a | 2010-04 | Found on Pastebay; appear to be malware-stolen. |
| Facebook (Pastebay) - w/ count | facebook-pastebay-withcount.txt.bz2 (407 bytes) | n/a | ||
| Unknown porn site | porn-unknown.txt.bz2 (30,600 bytes) | n/a | 2010-08 | Found on angelfire.com. No clue where they originated, but clearly porn site. |
| Unknown porn site - w/ count | porn-unknown-withcount.txt.bz2 (31,899 bytes) | n/a | ||
| Ultimate Strip Club List | tuscl.txt.bz2 (176,291 bytes) | n/a | 2010-09 | Thanks to Mark Baggett for finding! |
| Ultimate Strip Club List - w/ count | tuscl-withcount.txt.bz2 (182,441 bytes) | n/a | ||
| [Facebook Phished] | facebook-phished.txt.bz2 (14,457 bytes) | n/a | 2010-09 | Thanks to Andrew Orr for reporting |
| Facebook Phished - w/ count | facebook-phished-withcount.txt.bz2 (14,941 bytes) | n/a | ||
| Carders.cc | carders.cc.txt.bz2 (8,936 bytes) | n/a | 2010-05 | |
| Carders.cc - w/ count | carders.cc-withcount.txt.bz2 (9,774 bytes) | n/a | ||
| Singles.org | singles.org.txt.bz2 (50,697 bytes) | n/a | 2010-10 | |
| Singles.org - w/ count | singles.org-withcount.txt.bz2 (52,884 bytes) | n/a | ||
| Unnamed financial site | (reserved) | (reserved) | 2010-12 | |
| Unnamed financial site - w/ count | (reserved) | (reserved) | ||
| Gawker | (reserved) | (reserved) | 2010-12 | |
| Gawker - w/ count | (reserved) | (reserved) | ||
| Free-Hack.com | (reserved) | (reserved) | 2010-12 | |
| Free-Hack.com w/count | (reserved) | (reserved) | ||
| Carders.cc (second time hacked) | (reserved) | (reserved) | 2010-12 | |
| Carders.cc w/count (second time hacked) | (reserved) | (reserved) |
Statistics
I did some tests of my various dictionaries against the different sets of leaked passwords. I grouped them by the password set they were trying to crack:
Miscellaneous non-hacking dictionaries
These are dictionaries of words (etc), not passwords. They may be useful for one reason or another.
| Name | Compressed | Uncompressed | Notes |
| English | english.txt.bz2 (1,368,101 bytes) | n/a | My combination of a couple lists, from Andrew Orr, Brandon Enright, and Seth |
| German | german.txt.bz2 (2,371,487 bytes) | n/a | Compiled by Brandon Enright |
| American cities | us_cities.txt.bz2 (77,081 bytes) | n/a | Generated by RSnake |
| 'Porno' | porno.txt.bz2 (7,158,285 bytes) | n/a | World's largest porno password collection! Created by Matt Weir |
| Honeynet | honeynet.txt.bz2 (889,525 bytes) | n/a | From a honeynet run by Joshua Gimer |
| Honeynet - w/ count | honeynet-withcount.txt.bz2 (901,868 bytes) | n/a | |
| File locations | file-locations.txt.bz2 (1,724 bytes) | n/a | Potential logfile locations (for LFI, etc). Thanks to Seth! |
| Fuzzing strings (Python) | fuzzing-strings.txt.bz2 (276 bytes) | n/a | Thanks to Seth! |
| PHPMyAdmin locations | phpmyadmin-locations.txt.bz2 (304 bytes) | n/a | Potential PHPMyAdmin locations. Thanks to Seth! |
| Web extensions | web-extensions.txt.bz2 (117 bytes) | n/a | Common extensions for Web files. Thanks to dirb! |
| Web mutations | web-mutations.txt.bz2 (177 bytes) | n/a | Common 'mutations' for Web files. Thanks to dirb! |
DirBuster has some awesome lists, too -- usernames and filenames.
Facebook lists
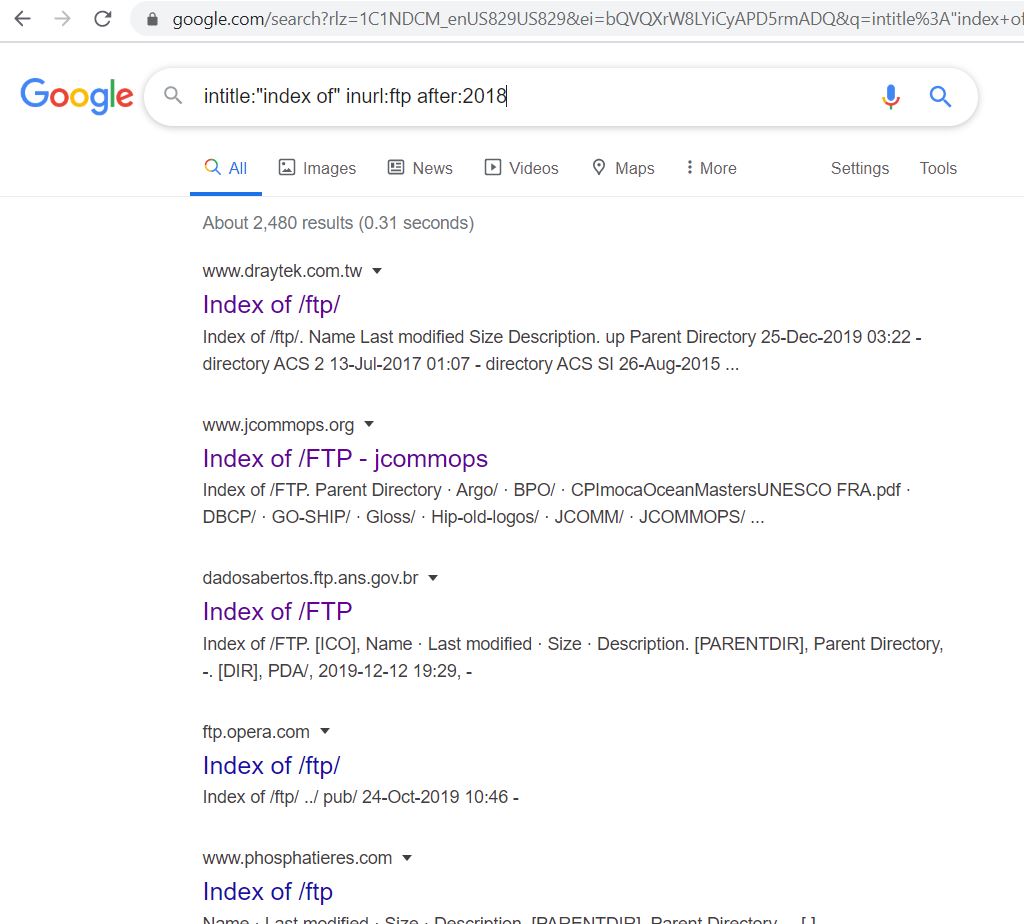
These are the lists I generated from this data. Some are more useful than others as password lists. All lists are sorted by commonness.
If you want a bunch of these, I highly recommend using the torrent. It's faster, and you'll get them all at once.
| Name | Compressed | Uncompressed | Date | Notes |
| Full names | facebook-names-unique.txt.bz2 (479,332,623 bytes) | n/a | 2010-08 | |
| Full names - w/ count | facebook-names-withcount.txt.bz2 (477,274,173 bytes) | n/a | ||
| First names | facebook-firstnames.txt.bz2 (16,464,124 bytes) | n/a | 2010-08 | |
| First names - w/ count | facebook-firstnames-withcount.txt.bz2 (73,134,218 bytes) | n/a | ||
| Last names | facebook-lastnames.txt.bz2 (21,176,444 bytes) | n/a | 2010-08 | |
| Last names - w/ count | facebook-lastnames-withcount.txt.bz2 (21,166,232 bytes) | n/a | ||
| First initial last names | facebook-f.last.txt.bz2 (67,110,776 bytes) | n/a | 2010-08 | |
| First initial last names - w/ count | facebook-f.last-withcount.txt.bz2 (66,348,431 bytes) | n/a | ||
| First name last initial | facebook-first.l.txt.bz2 (37,463,798 bytes) | n/a | 2010-08 | |
| First name last initial | facebook-first.l-withcount.txt.bz2 (36,932,295 bytes) | n/a |
STEALING PASSWORD WITH GOOGLE HACK
Google is a treasure trove full of important information, especially for the underground world. This Potential fact can also be utilized in the data for the username and password stored on a server.
If the administrator save important data not in the complete system authentifikasi folder, then most likely be reached by the google search engine. If data is successfully steal in by the unauthorized person, then the will be in misuse.
Here, some google search syntax to crawl the password:
1. 'Login: *' 'password =*' filetype: xls (searching data command to the system files that are stored in Microsoft Excel)

Intext Facebook Password Page
2. allinurl: auth_user_file.txt (to find files auth_user_file.txt containing password on server).
3. filetype: xls inurl: 'password.xls' (looking for username and password in ms excel format). This command can change with admin.xls)
4. intitle: login password (get link to the login page with the login words on the title and password words anywhere. If you want to the query index more pages, type allintitle)
5. intitle: 'Index of' master.passwd (index the master password page)

6. index of / backup (will search the index backup file on server)
7. intitle: index.of people.lst (will find web pages that contain user list).
8. intitle: index.of passwd.bak ( will search the index backup password files)
9. intitle: 'Index of' pwd.db (searching database password files).
10. intitle: 'Index of .. etc' passwd (this command will index the password sequence page).
11. index.of passlist.txt (will load the page containing password list in the clear text format).
12. index.of.secret (google will bring on the page contains confidential document). This syntax also changed with government query site: gov to search for government secret files, including password data) or use syntax: index.of.private
13. filetype: xls username password email (will find spreadsheets filese containing a list of username and password).
14. '# PhpMyAdmin MySQL-Dump' filetype: txt (will index the page containing sensitive data administration that build with php)
15. inurl: ipsec.secrets-history-bugs (contains confidential data that have only by the super user). or order with inurl: ipsec.secrets 'holds shared secrets'
16. inurl: ipsec.conf-intitle: manpage (useful to find files containing important data for hacking)
17. inurl: 'wvdial.conf' intext: 'password' (display the dialup connection that contain phone number, username and password)
18. inurl: 'user.xls' intext: 'password' (showing url that save username and passwords in spread sheet files)
19. filetype: ldb admin (web server will look for the store password in a database that dos not delete by googledork)
20.inurl: search / admin.php (will look for php web page for admin login). If you are lucky, you will find admin configuration page to create a new user.
21. inurl: password.log filetype:log (this keyword is to search for log files in a specific url)
22. filetype: reg HKEY_CURRENT_USER username (this keyword used to look for reg files (registyry) to the path HCU (Hkey_Current_User))
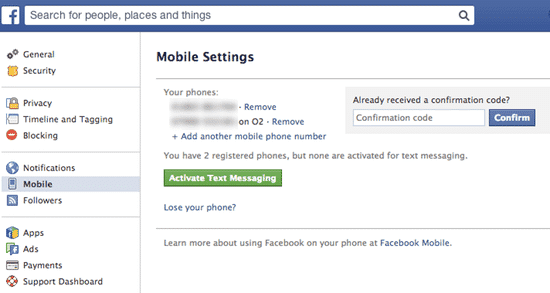
In fact, there are many more commands that google can crawl in use in the password. One who has the ability google reveals in this case is http://johnny.ihackstuff.com/. For that, visit the web to add insight about the google ability.
Here, some of the other syntax google that we need to look for confidential data :
'Http://username: password @ www ...' filetype: bak inurl: 'htaccess | passwd | shadow | ht users'
(this command is to take the user names and passwords for backup files)
filetype:mdb inurl:”account|users|admin|administrators|passwd|password” mdb files (this command is to take the password information)
filetype:ini ws_ftp pwd (searching admin password with ws_ftp.ini file)
intitle: 'Index of' pwd.db (searching the encrypted usernames and passwords)
inurl:admin inurl:backup intitle:index.of (searching directories whose names contain the words admin and backup)
“Index of/” “Parent Directory” “WS _ FTP.ini” filetype:ini WS _ FTP PWD (WS_FTP configuration files is to take FTP server access passwords)
ext:pwd inurl:(service|authors|administrators|users) “# -FrontPage-” (there is Microsoft FrontPage passwords)
filetype: sql ( 'passwd values ****' |' password values ****' | 'pass values ****') searching a SQL code and passwords stored in the database)
intitle:index.of trillian.ini (configuration files for the Trillian IM)
eggdrop filetype:user (user configuration files for the Eggdrop ircbot)
filetype:conf slapd.conf (configuration files for OpenLDAP)
inurl:”wvdial.conf” intext:”password” (configuration files for WV Dial)
ext:ini eudora.ini (configuration files for the Eudora mail client)
filetype: mdb inurl: users.mdb (potentially to take user account information with Microsoft Access files)
intext:”powered by Web Wiz Journal” (websites using Web Wiz Journal, which in its standard configuration allows access to the passwords file – just enter http:///journal/journal.mdb instead of the default http:///journal/)
“Powered by DUclassified” -site:duware.com 'Powered by DUclassified'-site: duware.com
“Powered by DUcalendar” -site:duware.com 'Powered by DUcalendar'-site: duware.com
“Powered by DUdirectory” -site:duware.com 'Powered by DUdirectory'-site: duware.com
“Powered by DUclassmate” -site:duware.com 'Powered by DUclassmate'-site: duware.com
“Powered by DUdownload” -site:duware.com 'Powered by DUdownload'-site: duware.com
“Powered by DUpaypal” -site:duware.com 'Powered by DUpaypal'-site:duware.com
“Powered by DUforum” -site:duware.com 'Powered by DUforum'-site: duware.com
intitle:dupics inurl:(add.asp | default.asp |view.asp | voting.asp) -site:duware.com (websites that use DUclassified, DUcalendar, DUdirectory, DUclassmate, DUdownload, DUpaypal, DUforum or DUpics applications, by default allows us to retrieve passwords file)
To DUclassified, just visit http:///duClassified/ _private / duclassified.mdb
or http:///duClassified/ or http:///duClassified/
intext: 'BiTBOARD v2.0' 'BiTSHiFTERS Bulletin Board' (Bitboard2 use the website bulletin board, the default settings make it possible to retrieve the passwords files to be obtained with the ways http:///forum/admin/data _ passwd.dat
or http:///forum/forum.php) or http:///forum/forum.php)
Searching for specific documents :
filetype: xls inurl: 'email.xls' (potentially to take the information contact)
Intext Password Txt
“phone * * *” “address *” “e-mail” intitle:”curriculum vitae”
CVs 'not for distribution' (confidential documents containing the confidential clause
buddylist.blt)
Intext Facebook Passwords
AIM contacts list AIM contacts list
intitle:index.of mystuff.xml intitle: index.of mystuff.xml
Trillian IM contacts list Trillian IM contacts list
filetype:ctt “msn” filetype: Note 'msn'
Intext Email Password Facebook
MSN contacts list MSN contacts list
filetype:QDF (QDF database files for the Quicken financial application)
intitle: index.of finances.xls (finances.xls files, potentially to take information on bank accounts, financial Summaries and credit card numbers)
Intext Facebook Password App
intitle: 'Index Of'-inurl: maillog (potentially to retrieve e-mail account)
