Talos said VPNFilter also targets a much larger number of devices than previously thought, including those made by ASUS, D-Link, Huawei, Ubiquiti, UPVEL, and ZTE. The malware also works on new. Over 500,000 routers and NAS systems in 54+ countries are now infected with new malware. The malware named “VPN Filter” is highly destructive and in the worst case can even destroy the infected device. (Please also read our updated article here with a list of affected devices)The US-American IT security company Talos, a subsidiary of the well-known router manufacturer Cisco, warns of a. GLAD TO SEE YOU HERE. SEE Vpn Filter Affected Router List And Vpn On Google Router IN BEST PRICES NOW. Norton Secure VPN helps prevent companies from tracking your online activities or location by encrypting your information on our no-log VPN. Browse the web anonymously from Internet service providers and cybercriminals. VPNFilter malware targets certain router models from these brands: Asus. Meaning VPN traffic bypasses interface access-lists (Version 7.1 (1)+ Changes this command to sysopt connection permit-vpn) VPN filters permits or denies traffic both BEFORE it enters the tunnel (pre-encrypted) and AFTER it exits the tunnel (post encrypted).
VPNFilter is malware designed to infect routers and certain network attached storage devices. As of 24 May 2018, it is estimated to have infected approximately 500,000 routers worldwide, though the number of at-risk devices is larger.[1] It can steal data, contains a 'kill switch' designed to disable the infected router on command, and is able to persist should the user reboot the router.[2] The FBI believes that it was created by the Russian Fancy Bear group.[3][4]
Operation[edit]
VPNFilter is malware infecting a number of different kinds of network routers and storage devices. It seems to be designed in part to target serial networking devices using the Modbus protocol to talk to and control industrial hardware, as in factories and warehouses. The malware has special, dedicated code to target control systems using SCADA.[5]
The initial infection vector is still unknown. The Cisco Talos security group hypothesizes the malware exploits known router security vulnerabilities to infect devices[6].
This software installs itself in multiple stages:
- Stage 1 involves a worm which adds code to the device's crontab (the list of tasks run at regular intervals by the cron scheduler on Linux). This allows it to remain on the device after a reboot, and to re-infect it with the subsequent stages if they are removed. Stage 1 uses known URLs to find and install Stage 2 malware. If those known URLs are disabled, Stage 1 sets up a socket listener on the device and waits to be contacted by command and control systems.[7]
- Stage 2 is the body of the malware, including the basic code that carries out all normal functions and executes any instructions requested by special, optional Stage 3 modules.
- Stage 3 can be any of various 'modules' that tell the malware to do specific things, like spying on industrial control devices (Modbus SCADA) or using anonymity network Tor protocol to communicate over encrypted traffic channels.[5]
What it does[edit]
VPNFilter uses multiple third stage operations after the initial infection. One such function of VPNFilter is to sniff network data on a network connected to the infected device, and gather credentials, supervisory control and data. The data are then encrypted and exfiltrated via the Tor network.
It can also serve as a relay point to hide the origin of subsequent attacks.
Mitigation[edit]
Both Cisco and Symantec suggest that people who own affected devices do a factory reset. That is typically accomplished by using a small, pointed object, such as a straightened out paperclip, to push the small reset button on the back on the unit for 10 to 30 seconds (time varies by model). This will remove the malware, but also restores the router to all original settings. If the router has remote management enabled, a factory reset will often disable this (the default setting of many routers). Remote management is thought to be one possible vector for the initial attack.
Before connecting the factory-reset router to the internet again, the device's default passwords should be changed to prevent reinfection[8].
Devices at risk[edit]
The initial worm that installs VPNFilter can only attack devices running embedded firmware based on Busybox on Linux compiled only for specific processors. This does not include non-embedded Linux devices such as workstations and servers.[9]
Manufacturer-provided firmware on the following router models is known to be at risk:[10][7]
- Asus
- RT-AX92U
- RT-AC66U
- RT-N10
- RT-N10E
- RT-N10U
- RT-N56U
- RT-N66U
- D-Link
- DES-1210-08P
- DIR-300
- DIR-300A
- DSR-250N
- DSR-500N
- DSR-1000
- DSR-1000N
- Huawei
- HG8245
- Linksys
- E1200
- E2500
- E3000
- E3200
- E4200
- RV082
- WRVS4400N
- Mikrotik
- CCR1009
- CCR1016
- CCR1036
- CCR1072
- CRS109
- CRS112
- CRS125
- RB411
- RB450
- RB750
- RB911
- RB921
- RB941
- RB951
- RB952
- RB960
- RB962
- RB1100
- RB1200
- RB2011
- RB3011
- RB Groove
- RB Omnitik
- STX5
- Mikrotik RouterOS versions up to 6.38.5 on current or 6.37.5 on bugfix release chains[11]
- Netgear
- DG834
- DGN1000
- DGN2200
- DGN3500
- FVS318N
- MBRN3000
- R6400
- R7000
- R8000
- WNR1000
- WNR2000
- WNR2200
- WNR4000
- WNDR3700
- WNDR4000
- WNDR4300
- WNDR4300-TN
- UTM50
- QNAP
- TS251
- TS439 Pro
- Other QNAP NAS devices running QTS software
- TP-Link
- R600VPN
- TL-WR741ND
- TL-WR841N
- Ubiquiti
- NSM2
- PBE M5
- Upvel
- Unknown Models [nb 1]
- ZTE
- ZXHN H108N
Epidemiology[edit]
VPNFilter is described by Cisco Talos as having infected as many as 500,000 devices worldwide,[9] in perhaps 54 different countries, though proportionately the focus has been on Ukraine.
FBI investigation[edit]
The FBI has taken a high-profile role in addressing this malware, conducting an investigation that resulted in the seizure of the domain name toknowall.com as ostensibly having been used to redirect queries from stage 1 of the malware, allowing it to locate and install copies of stages 2 and 3.[4] The US Justice Department also compelled the site Photobucket to disable known URLs used to distribute malware Stage 2.[6][12]
FBI recommendation on removing the infection[edit]
On 25 May 2018, the FBI recommended that users reboot their at-risk devices.[13] This would temporarily remove the stages 2 and 3 of the malware. Stage 1 would remain, leading the router to try re-downloading the payload and infecting the router again. However, prior to the recommendation the US Justice Department seized web endpoints the malware uses for Stage 2 installation.
Without these URLs, the malware must rely on the fallback socket listener for Stage 2 installation. This method requires threat actor command and control systems to contact each system to install Stage 2, increasing the threat actor's risk of being identified.[6] The FBI further recommended users disable remote management on their devices and update the firmware. A firmware update removes all stages of the malware, though it is possible the device could be reinfected.[13]
The FBI said that this would help them to find the servers distributing the payload.[14][15][3]
Notes[edit]
- ^Malware targeting Upvel as a vendor has been discovered, but we[who?] are unable to determine which specific device it is targeting.
References[edit]
- ^'VPNFilter Update and Our First Summit Recap'. Cisco Talos Intelligence. 2018-06-21. Retrieved 2018-06-26.
- ^'VPNFilter state-affiliated malware pose lethal threat to routers'. SlashGear. 2018-05-24. Retrieved 2018-05-31.
- ^ abKevin Poulsen (23 May 2018). 'Exclusive: FBI Seizes Control of Russian Botnet'. Daily Beast.
- ^ abFBI to all router users: Reboot now to neuter Russia's VPNFilter malware
- ^ abVPNFilter: New Router Malware with Destructive Capabilities
- ^ abc'VPNFilter, the Unfiltered Story'. Talos. 2018-05-29. Retrieved 2018-06-26.
- ^ abWilliam Largent (6 June 2018). 'VPNFilter Update - VPNFilter exploits endpoints, targets new devices'.
- ^'Security Advisory for VPNFilter Malware on Some NETGEAR Devices'. Netgear. 2018-06-06. Retrieved 2018-06-26.
- ^ ab'Hackers infect 500,000 consumer routers all over the world with malware'. Ars Technica. Retrieved 2018-05-31.
- ^'VPNFilter: New Router Malware with Destructive Capabilities'. Retrieved 2018-05-31.
- ^'VPNfilter official statement - MikroTik'. forum.mikrotik.com. Retrieved 2018-05-31.
- ^'AFFIDAVIT IN SUPPORT OF AN APPLICATION FOR A SEIZURE WARRANT'. 22 May 2018.
- ^ ab'FOREIGN CYBER ACTORS TARGET HOME AND OFFICE ROUTERS AND NETWORKED DEVICES WORLDWIDE'. 25 May 2018.
- ^Dan Goodin (25 May 2018). 'FBI tells router users to reboot now to kill malware infecting 500k devices'. Ars Technica.
- ^Dan Goodin (24 May 2018). 'Hackers infect 500,000 consumer routers all over the world with malware'. Ars Technica.
Note: You are viewing the documentation for an older major version of the AWS CLI (version 1).
AWS CLI version 2, the latest major version of AWS CLI, is now stable and recommended for general use. To view this page for the AWS CLI version 2, click here. For more information see the AWS CLI version 2 installation instructions and migration guide.
[ aws . ec2 ]
Description¶
Describes one or more of your virtual private gateways.
For more information, see AWS Site-to-Site VPN in the AWS Site-to-Site VPN User Guide .
See also: AWS API Documentation
See 'aws help' for descriptions of global parameters.
Synopsis¶
Options¶
--filters (list)
One or more filters.
- amazon-side-asn - The Autonomous System Number (ASN) for the Amazon side of the gateway.
- attachment.state - The current state of the attachment between the gateway and the VPC (attaching | attached | detaching | detached ).
- attachment.vpc-id - The ID of an attached VPC.
- availability-zone - The Availability Zone for the virtual private gateway (if applicable).
- state - The state of the virtual private gateway (pending | available | deleting | deleted ).
- tag :key- The key/value combination of a tag assigned to the resource. Use the tag key in the filter name and the tag value as the filter value. For example, to find all resources that have a tag with the key Owner and the value TeamA , specify tag:Owner for the filter name and TeamA for the filter value.
- tag-key - The key of a tag assigned to the resource. Use this filter to find all resources assigned a tag with a specific key, regardless of the tag value.
- type - The type of virtual private gateway. Currently the only supported type is ipsec.1 .
- vpn-gateway-id - The ID of the virtual private gateway.
(structure)
A filter name and value pair that is used to return a more specific list of results from a describe operation. Filters can be used to match a set of resources by specific criteria, such as tags, attributes, or IDs. The filters supported by a describe operation are documented with the describe operation. For example:
- DescribeAvailabilityZones
- DescribeImages
- DescribeInstances
- DescribeKeyPairs
- DescribeSecurityGroups
- DescribeSnapshots
- DescribeSubnets
- DescribeTags
- DescribeVolumes
- DescribeVpcs
Name -> (string)
Values -> (list)
The filter values. Filter values are case-sensitive.
(string)
Shorthand Syntax:
JSON Syntax:
--vpn-gateway-ids (list)
One or more virtual private gateway IDs.
Default: Describes all your virtual private gateways.
(string)
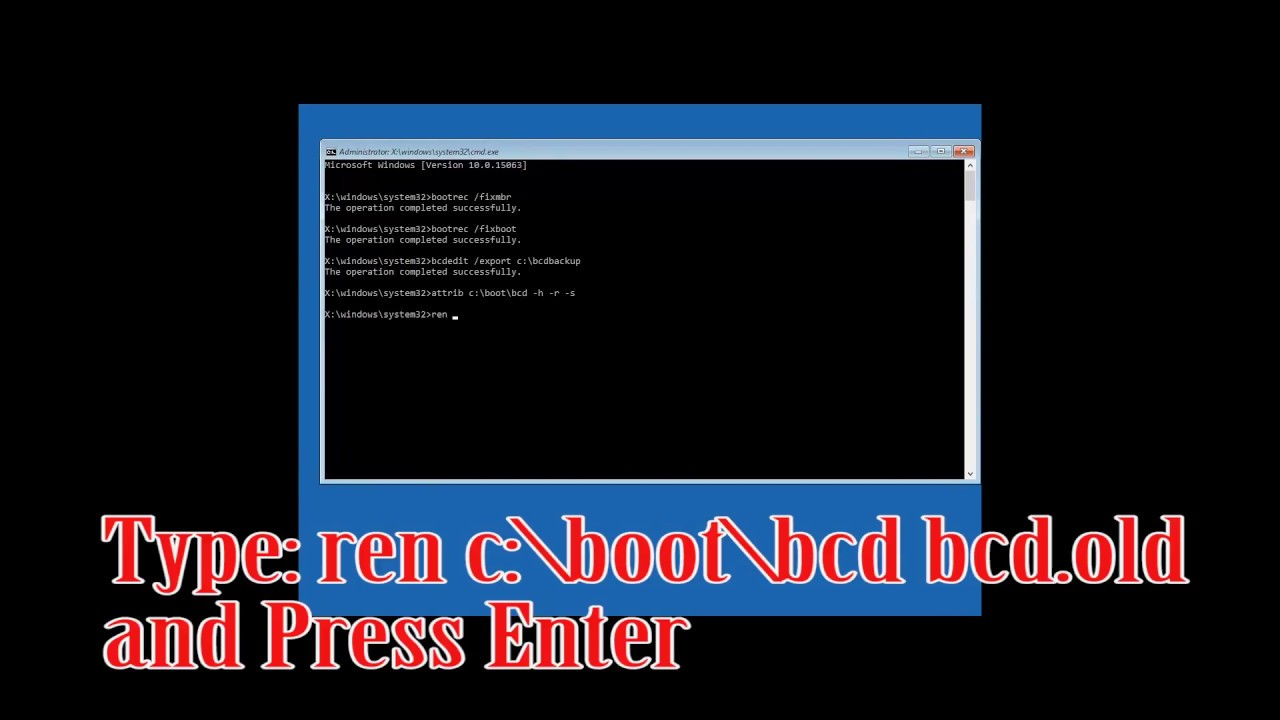
Cisco Asa Vpn Filter
Syntax:
--dry-run | --no-dry-run (boolean)
--cli-input-json (string)Performs service operation based on the JSON string provided. The JSON string follows the format provided by --generate-cli-skeleton. If other arguments are provided on the command line, the CLI values will override the JSON-provided values. It is not possible to pass arbitrary binary values using a JSON-provided value as the string will be taken literally.
--generate-cli-skeleton (string)Prints a JSON skeleton to standard output without sending an API request. If provided with no value or the value input, prints a sample input JSON that can be used as an argument for --cli-input-json. If provided with the value output, it validates the command inputs and returns a sample output JSON for that command.
See 'aws help' for descriptions of global parameters.
Examples¶
To describe your virtual private gateways
This example describes your virtual private gateways.
Command:
Output:
Output¶
VpnGateways -> (list)
Information about one or more virtual private gateways.
(structure)
Describes a virtual private gateway.
AvailabilityZone -> (string)
State -> (string)
Type -> (string)
VpcAttachments -> (list)
Any VPCs attached to the virtual private gateway.
(structure) Adobe reader x64 fixes v3.
Describes an attachment between a virtual private gateway and a VPC.

State -> (string)
VpcId -> (string)
VpnGatewayId -> (string)
AmazonSideAsn -> (long)
Vpn Filter Malware Check
Tags -> (list)
Any tags assigned to the virtual private gateway.
(structure) Checksoft® premier 14 - download.
Describes a tag.
Key -> (string)
The key of the tag.
Constraints: Tag keys are case-sensitive and accept a maximum of 127 Unicode characters. May not begin with aws: .
Vpn Filter Check Tool
Value -> (string)
The value of the tag.
Constraints: Tag values are case-sensitive and accept a maximum of 255 Unicode characters.