
When creating VPNs in Cisco ASA Firewall a very important configuration to be in mind it's the sysopt connection permit-vpn.
“sysopt connection preserve-vpn-flows” This commands allows the VPN to preserve the TCP state across the tunnel during re-keying. I added this statement to the tunnel, and it cleared up the drops the customer was having. If you have a VPN to a cloud provider from a Cisco ASA, make sure that this command is on your ASA. Hi, We have couple of VPN Tunnels and at present we are not able to restrict VPN tunnel traffic in ASA. We are planing to remove sysopt connection permit-vpn from ASA so VPN tunnel traffic we can restrict using inside and outside ACL's. If you searching to check Sysopt Connection Permit Vpn And Vpn 1 Click For Pc price.
When enabled the commands allow packets from an IPsec tunnel and their payloads to bypass interface ACLs on the security appliance. In other works, the traffic will bypasss the access lists configured in the interfaces, so it will be no necessary to explicitly allow the traffic.
Windows 10 Connect Vpn Automatically And Asa Sysopt Connection Permit Vpn is best in online store. Sysopt connection permit-vpn When creating VPNs in Cisco ASA Firewall a very important configuration to be in mind it's the sysopt connection permit-vpn. When enabled the commands allow packets from an IPsec tunnel and their payloads to bypass interface ACLs on the security appliance.
To verify if it is enable you have to perform the show run all sysopt
Sysopt Connection Permit-vpn Command Reference
command:| ASA# show running-config all sysopt no sysopt connection timewait sysopt connection tcpmss 1380 sysopt connection tcpmss minimum 0 no sysopt nodnsalias inbound no sysopt nodnsalias outbound no sysopt radius ignore-secret sysopt connection permit-vpn |
In case you want to filter the traffic encapsulated, you have to use the
Sysopt Connection Permit-vpn Asdm
vpn-filter command in the group policy attributes and applied to the tunnel-group associated with the VPN you are configuring: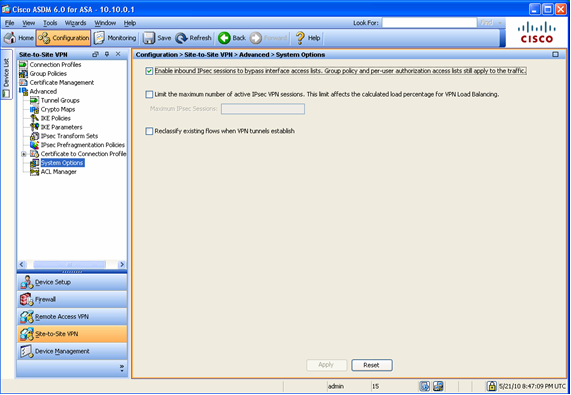
| access-list 100 extended deny tcp any host 10.10.1.10 eq 80 access-list 100 extended permit ip any any group-policy CustomerA internal group-policy CustomerA attributes vpn-filter value 100 tunnel-group 172.16.1.1 general-attributes default-group-policy CustomerA |
